As businesses large and small deal with widespread cyberattacks, it’s important to learn about the most common cybersecurity threats, such as ransomware, how to prevent them at your business or organization, and steps to take if your business is attacked.
Two experts joined us on an episode of the First Business Bank Podcast (How To Protect Your Business From Cyberattacks) to discuss common types of cybersecurity threats, how to prevent cyberattacks, what to look for in cybersecurity insurance, how much coverage businesses need, and how it works.
- Frank Stephens founded Computing Technology Solutions in 2001 and is a cybersecurity expert who works with businesses to help them protect their operations from fraud. His company also helps clients recover from cyberattacks.
- Derek Laczniak, partner at M3 insurance who is a cybersecurity insurance expert, heads their cyber liability efforts to help businesses reduce their risk of loss from cyberattacks like ransomware.
86% Of Cyberattacks Caused By Employee Negligence
While most of us think that backup servers and firewalls can prevent cyberattacks, unfortunately, that’s increasingly more difficult, as human employees often are the weakest link.
“We can build the strongest doors, but if one of our employees is doing something potentially negligent, that’s where 86% of cyberattacks happen,” said Stephens. It happens in all types of businesses, the experts said.
From the banking side, the most sophisticated banking fraud prevention solutions can’t stop your employees from clicking on a malicious link in an email or website or stop your employees from sending a payment to a cyber-criminal impersonating a vendor. Due diligence and training within your organization are key to cyberattack prevention.
From the banking side, the most sophisticated banking fraud prevention solutions can’t stop your employees from clicking on a malicious link in an email or website or stop your employees from sending a payment to a cyber-criminal impersonating a vendor. Due diligence and training within your organization are key to cyberattack prevention. The Cybersecurity & Infrastructure Security Agency recommends all organizations, no matter the size, implement a cybersecurity awareness training program to help employees learn how to identify and report suspicious cybersecurity threats, such as malicious email. The governmental agency’s Ransomware Guide can help your business plan out your own strategy to strengthen your cyberattack prevention and response initiatives.
Funds Lost To Ransomware Attacks Rise By 74%
Ransomware attacks, which happen when malware gains access to your device and encrypts data, holding it hostage for ransom, are becoming more sophisticated. In its 2023 Internet Crime Report, the Federal Bureau of Investigations (FBI) says the number of ransomware attacks rose 18% and funds lost to ransomware attacks grew 74% in 2023.
“Ransomware attacks are growing more concerning and stronger over the last few years,” said Derek Laczniak with M3 Insurance. “Ransomware used to involve holding your information hostage in exchange for a payment in crypto currency. Then businesses started working with organizations like Frank's and installing sophisticated backups, so now if you don't pay, even if you restore your backup data, they threaten to dump everything online.”
Inbox Compromise Drives Large Fraud Loss
While ransomware is widespread and growing quickly, Derek Laczniak said losses from ransomware attacks aren’t usually as catastrophic as fraud resulting from inbox compromise.
“Inbox compromises have caused the largest losses,” Laczniak said. “Bad actors usually want to use the data to commit fraud. When it happens, everything in your inbox should be presumed to be stolen.”
When inbox compromise happens, cyber-criminals gain undetected access to an email inbox and sometimes monitor the data coming and going for months, using it to commit complex fraud schemes.
“Someone gets into the backend; they infiltrate the mailbox and put rules in place, so they see copies of all inbound and outbound email,” said Frank Stephens. “They sit there for months and create a phony email account that looks like the controller’s or CFO’s address. Then, for instance, they send an email to a bank asking to wire money. You'd be surprised how authentic these emails look. They are getting smarter and smarter, and it looks legit. They've been watching and have all our data for months on end.”
Who Is A Victim Of Cyberattacks?
While the larger data breaches and governmental cyberattacks make headlines, our experts see smaller organizations as the latest target.
“They’re targeting organizations with 10 to 150 employees,” said Stephens. “They may not have a huge budget for cybersecurity, so they’re an easier target and less likely to have tools in place for awareness training. Unfortunately, when they do get hit, it shuts down their business. They can, and they do, go out of business.”
 “They go after the weakest companies,” said Laczniak. They know they can't ask for as much ransom, but there’s a higher probability of executing a payload. Construction has largely believed they are immune, but if you go to a jobsite, you'll notice the foreman has an iPad. Their technology has advanced, and they’ve been affected.
“They go after the weakest companies,” said Laczniak. They know they can't ask for as much ransom, but there’s a higher probability of executing a payload. Construction has largely believed they are immune, but if you go to a jobsite, you'll notice the foreman has an iPad. Their technology has advanced, and they’ve been affected.
“On the manufacturing floor, you have CNC machines timed to an ERP system,” Laczniak said. “They’re being told what to make through computer software. You take it offline for three weeks and they pay ransoms. We’ve seen an uptick in manufacturers getting hit hard with ransomware.”
How Businesses Recover From A Cyberattack
The best chance to minimize fraud loss is to start out prepared. It’s important that businesses drastically cut down response time by having a plan to follow if they discover they’re victims of inbox compromise, ransomware, or another fraud scheme.
“You need an instant response,” said Stephens. “Know who to alert and the process to follow. My organization can quarterback the whole thing, bringing in law enforcement and forensics experts, preserving the data, and providing data that we find to law enforcement and insurance. Time is essential and preserving the data is essential as well.”
Laczniak agrees that time is of the essence when a business or organization is hit by a cyberattack. “When you’re dealing with a social engineered transaction, it's all about time,” Laczniak said. “The quicker you notify your financial institution, the greater chance you have to get your money back. You have a window of time to chase it around before it goes through nine different bank accounts. With inbox compromise and ransomware, it’s all about how ready you are and how quickly you can respond, so have a plan in place.”
From First Business Bank’s point of view, the faster clients contact us, the better. We always recommend implementing fraud prevention solutions and strong security controls, such as following strict internal controls for all monetary transactions and vigilant account monitoring.
Recovering From Ransomware Attacks
In a ransomware attack, immediately identify the computer or server involved. “Isolate patient zero, and immediately turn it off and disconnect it from your network,” said Stephens. “Take an immediate snapshot of the server prior to that. If the cyber-criminal has access to the backups, they can delete that data as well. Focus on preserving logs of all the systems — the firewalls, logs from the servers, and endpoint detection systems. Preserve the logs and integrity of the data at the time of the attack so you can provide it to your insurance company, legal, and federal officials.”
On paying a ransom to the cyberthieves, our experts recommend against it. “The feedback is you should never pay a ransom,” Stephens said. “When they get millions, they continue to increase their hits. If you've been hit once, the likelihood of being hit again is multiplied based on several factors.”
Preplanning reduces the steps and time it takes to recover, said Laczniak. “Know, in advance, the tools that are available to you,” Laczniak said. “Cyber breaches have a predictable pattern regardless of the attack. In the best recoveries, 99% of breaches have included a breach coach and a forensics analysis firm. A breach coach is a highly specialized attorney that helps you protect your company. You're open to civil and regulatory ligation down the line, so you don't want every conversation subject to recovery. Know who you call first so you can turn something that could be 48 hours into four hours.”
What’s In A Cybersecurity Insurance Policy?
Cybersecurity insurance policies reimburse you for cyber-related fraud, such as data breaches and ransomware attacks. Data from the U.S. Government Accountability Office (GAO) shows that, even as premiums rise due to increasing fraud loss, more insurance clients are opting in for cybersecurity insurance coverage. In 2016, only 26% of insurance clients got cybersecurity insurance, but in 2020, that number grew to 47%.
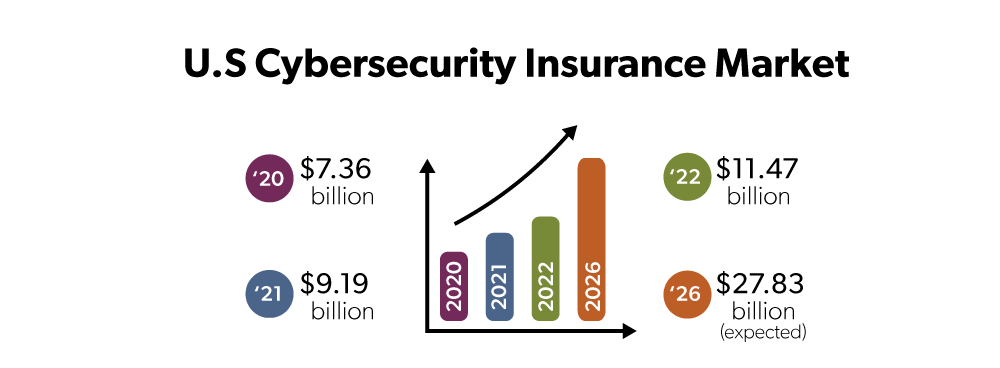
“Cybersecurity insurance has really evolved and became mainstream about 20 years ago,” said Derek Laczniak of M3 Insurance. It turned into a $5 billion market that could rival the property insurance market. Cybersecurity insurance rates have risen 50 to 100% over the last few years. Coverage still remains broad, but we’ve seen some carriers start to retract coverage. The devil is in the details.”
Laczniak said that the fast-changing landscape of cyber fraud challenges insurance companies. “Even as risk management evolves, attackers continue to evolve,” he said. “We're used to dealing with finite risks like fire, wind, and hail. In cyber, we’re designing and pricing policies to battle a risk that changes every three months. It’s a moving target that’s becoming more severe.”
Things to know about most cybersecurity insurance policies:
- It covers your expenses to remediate. Cybersecurity insurance policies often pay for an attorney, for a company like Computing Technology Solutions, LLC, recover income lost, pay a ransom, and all first-party costs related to the incident.
- It pays for any liability because of a data security incident. For instance, if a ransomware attack caused your clients’ data to be exposed and they are now suing your business, many cybersecurity insurance policies cover those damages.
- There’s no industry standard in cybersecurity insurance policies. Insurance carriers all use different language in their policies, so it’s important to read the details to understand what you’re really getting. “They are all set up differently,” Laczniak said.
Cybersecurity: What Business Owners Should Know
Stephens said the supply chain volatility has affected the cybersecurity recovery industry and their clients.
“The smallest supply chain disruption of external hard drives can affect businesses,” he said. “Not long ago, there was a shortage of external terabyte drives; they just weren’t on the shelf. In a recovery, you’re making an image copy of the infected servers and if you don’t have external terabyte servers sitting around, you couldn’t get them. That's a little thing you can have on hand, just in case. Check all the bases — do you have everything you need?”
Be proactive. When you have the appropriate documentation, and follow the checklist, you're going to have a minimal attack. Make sure you have a full security stack that protects everything from your servers to the internet and down to the end user. Stephens recommends:
- Use end point detection response (EDR). This is “virus protection on steroids.” Virus protection is software that has a definition file. End point protection takes it to the next level. It prohibits and stops a ransomware attack. It learns your behavior and what websites end users are visiting. If something is outside of their profile, the EDR says, “Hey, something doesn't smell right,” and shuts that process down. It’s a game changer.
- Evaluate a back-up disaster recovery solution. In the event of a natural disaster, is your data in the cloud and secure?
- Set-up multifactor authentication (MFA). To log in to all your banking solutions, make sure to set up MFA with a pin or code emailed to you. “If you do not have MFA in place externally, you're a sitting duck,” Stephens said.
- Enroll in Microsoft spam protection. Use a front layer of phishing and spam protection; it’s a few dollars a month, Stephens said.
- Mandate an employee cybersecurity awareness training program. “86% of hackings are because an employee or contractor does something they shouldn’t have done,” Stephens said. “The training can be 10 to 15 minutes a year and cover what not to do.”
- Implement patch management. Patch management is ongoing updates to software, drivers, and firmware that fixes identified vulnerabilities. “In an attack, that’s what they use to spread them,” Stephens said. “If you have a Mac, it’s not true that they don’t experience cyberattacks."
Those six steps, Stephens said, should help reduce the likelihood that you’ll experience a ransomware attack, but they’re also required to apply for cybersecurity insurance, said Laczniak.
“Those six items have gone from nice-to-haves to table stakes to apply for cyber insurance,” Laczniak said. “Eight years ago, they gave cyber insurance away. Now, I really care about the answers to those questions.”
Laczniak also recommended becoming familiar with your cyber insurance policy, instead of buying it and ignoring it.
“A lot of people buy cyber insurance policies, and putting it on the shelf is not enough,” he said. You need to know can a firm like Frank’s be approved? What are the limits? What do you have to submit so they'll pay the expenses? What forensics company can you use? Shrink that time to respond as much as possible. A little homework on the front end limits the impact of the attacks.”





