Protecting businesses and their stakeholders from cybercriminals requires staying ahead of fraud trends and implementing comprehensive education about prevention strategies. Two common threats, smishing and phishing, exploit organizations and individuals through deceptive text messages and emails designed to gather sensitive information.
Phishing attacks utilize fraudulent emails to trick people into clicking malicious links or revealing personal or company information, while smishing employs SMS text messages that impersonate legitimate communications, attempting to lure individuals into clicking suspicious links or calling scam phone numbers.
These attacks can lead to lost personal funds and information, but also devastate businesses, causing compromised bank accounts, stolen customer data, ransomware infections, and significant financial losses that can drastically affect a business’s operations.
How Do Smishing & Phishing Work?
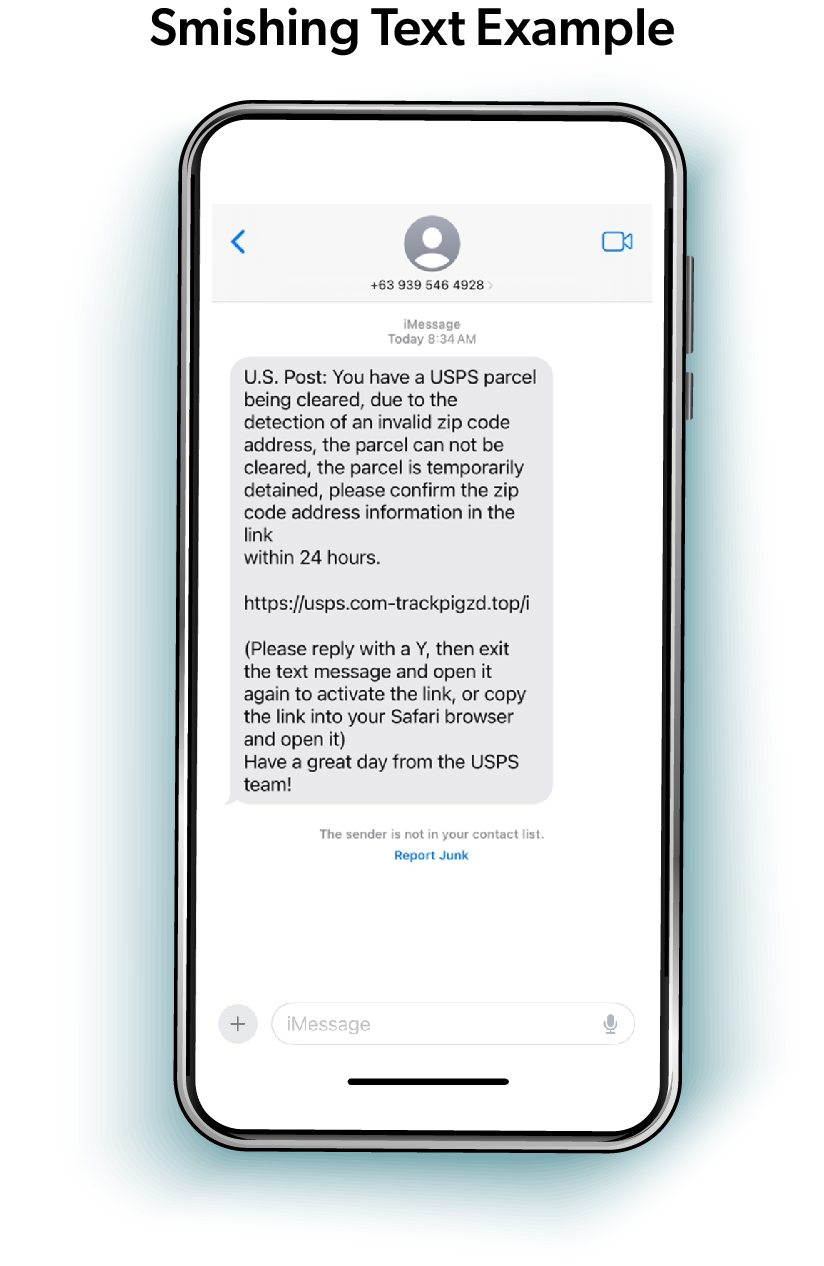 Cybercriminals increasingly target both individuals and businesses through email and text messages, knowing that just one successful attack can get them the funds or the sensitive information they want. By pretending to be a vendor, a company, or even a grandchild, these criminals try to get sensitive data ranging from personal financial account information to corporate systems and customer databases.
Cybercriminals increasingly target both individuals and businesses through email and text messages, knowing that just one successful attack can get them the funds or the sensitive information they want. By pretending to be a vendor, a company, or even a grandchild, these criminals try to get sensitive data ranging from personal financial account information to corporate systems and customer databases.
Common tactics range from creating a false sense of urgency around financial matters to impersonating business partners with fake contract issues. Scammers frequently send fake delivery notifications, payment requests, and account verification messages. They've also become adept at hiding malicious links through website link shorteners and using email addresses that look very much like legitimate domain addresses. Scammers' strategies have grown more sophisticated, partly due to artificial intelligence, making these messages harder to detect.
How To Identify Smishing & Phishing Attempts
Protecting organizations from cyber threats requires understanding the common characteristics of these attacks. The first line of defense against smishing texts and phishing emails (also known as business email compromise or BEC) is ensuring all team members can identify suspicious messages. Here are some common traits:
Smishing Text Red Flags
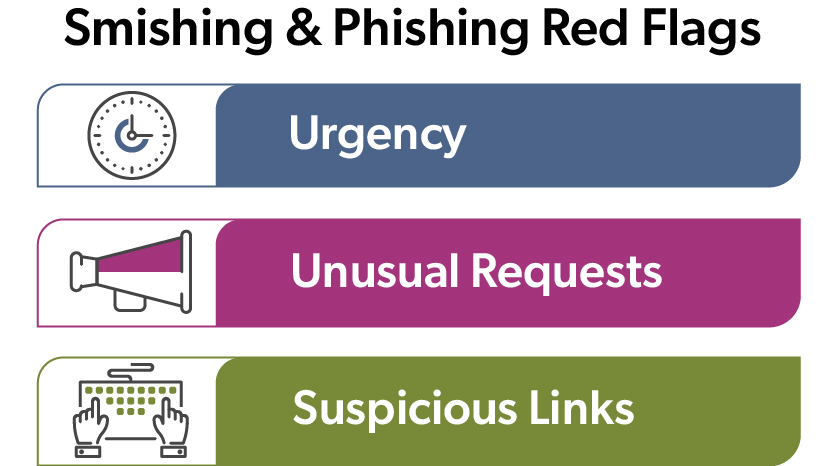 Unexpected, urgent texts about business accounts or payments
Unexpected, urgent texts about business accounts or payments - Texts appearing to be from your financial institution about unauthorized transactions that prompt you to click a malicious link or provide sensitive information
- Texts masquerading as a toll operator about past-due tolls, prompting you to click a malicious link to pay
- Texts or phone calls claiming to be a grandchild or relative in urgent need of money
- Shortened URLs masking suspicious website links
- Any texts requiring immediate financial decisions or asking for sensitive information (personal or business)
- Requests to call unfamiliar numbers about personal financial or business matters
Phishing Email Red Flags
- Urgent emails about financial matters requiring immediate action
- Emails impersonating family members, especially targeting Private Wealth clients, with urgent financial requests
- Threats about accounts, taxes, or compliance issues
- Emailed financial requests that bypass normal business processes
- Suspicious attachments or links to unfamiliar websites
- Subtle misspellings in sender addresses or domains
Beware of Financial Institution Impersonation Scams
Cybercriminals frequently impersonate financial institutions, including First Business Bank, to trick people into sharing sensitive information. These scams, often conducted through smishing, phishing, and fraudulent phone calls, often create a false sense of urgency to pressure recipients into providing confidential details.
Fraudsters may spoof legitimate bank phone numbers, making it appear as though their messages or calls are coming from a trusted source. They may claim an account has been compromised, a suspicious transaction needs verification, or immediate action is required to prevent a financial loss. In reality, their goal is to obtain login credentials, account numbers, or one-time passcodes that give them direct access to funds.
These scam tactics are always evolving, but here are some tips to help protect businesses and individuals from bank impersonation scams:
- Know financial institutions' practices. First Business Bank will never request account numbers, online banking credentials, tax IDs or Social Security numbers, passwords, or PINs through unsolicited calls, emails, or texts. Treat any such requests as highly suspicious.
- Verify unexpected requests. Recipients of suspicious messages claiming to be their financial institution should contact their financial institution using a known phone number rather than responding to texts, emails, or phone calls.
- Never share one-time passwords or PINs. These codes are for personal use only and should not be disclosed to anyone, even if the request appears legitimate.
Do not engage with suspicious communications claiming to be from your financial institution. Instead document the contact details and immediately report it to your financial institution. If you are a First Business Bank client, please contact the Treasury Management support team at 608-232-5938.
What Are Potential Consequences Of Clicking On Malicious Links?
 For businesses, phishing and smishing attacks can devastate operations through multiple channels, and direct financial losses from unauthorized transactions are just the beginning. Companies often face legal fees, costs from implementing emergency security measures, and potential regulatory fines for failing to protect sensitive data. Beyond immediate financial impact, these security breaches can paralyze operations, leading to lost productivity while systems are secured. The reputational fallout can be equally severe as customers lose trust in your business to keep their data safe. This loss of confidence often leads to lost clients, damaged business relationships, and skeptical investors, creating long-term challenges for growth and stability.
For businesses, phishing and smishing attacks can devastate operations through multiple channels, and direct financial losses from unauthorized transactions are just the beginning. Companies often face legal fees, costs from implementing emergency security measures, and potential regulatory fines for failing to protect sensitive data. Beyond immediate financial impact, these security breaches can paralyze operations, leading to lost productivity while systems are secured. The reputational fallout can be equally severe as customers lose trust in your business to keep their data safe. This loss of confidence often leads to lost clients, damaged business relationships, and skeptical investors, creating long-term challenges for growth and stability.
For individuals, the consequences can be personally destructive. Clicking malicious links can lead to drained bank accounts, stolen credit card information, and compromised personal data that takes months or years to fix. Particularly heartbreaking are grandparent scams, where criminals pose as grandchildren in desperate situations — claiming to be injured, jailed, or stranded abroad - and urgently requesting wire transfers. These scams exploit emotional connections to steal life savings, often leaving victims not only financially damaged but also deeply distressed. Recovering from personal cyber-attacks can involve lengthy battles to fix identity theft, creating financial hardship and emotional trauma.
What To Do With Suspicious Messages & Emails
Never click links in suspicious emails or unexpected text messages, even if they appear to be from a bank or a known business. Instead:
- Send suspicious texts to 7726 (SPAM), which allows wireless companies to track and block scammers.
- Delete suspicious messages after reporting them.
- Contact legitimate banks, companies, and relatives using their official contact information (not from the scam message) from a previous invoice, statement, corporate website, or from another relative.
- Never share sensitive business or personal information via email or text.
- Keep all your cell phones, mobile devices, and computers up to date with security features updated.
- Slow down and verify unusual requests through established channels.
- Access all business and personal accounts only through official websites.
Smishing and phishing attempts are incredibly common, so it's important to thoroughly scrutinize all communications. If a message creates pressure to act quickly or contains any suspicious elements, verify it through official channels. Make sure all team members understand that exercising caution when facing potential cybersecurity threats is always preferable to compromising business security. Visit our fraud prevention page for more up-to-date tips about how to prevent fraud.





