In today’s digital age with the prominence of social media, targeted email phishing has become increasingly common in aiding wire transfer fraud. Wire transfers continue to be an attractive target of fraudulent activity due to the speed and finality of payment, as well as the lack of internal controls and employee education in how to avoid wire transfer fraud. Fraudsters know that money wired is nearly impossible to recover because of immediate settlement and availability of those funds. Wire transfer fraud is an epidemic that is reaching historic levels throughout the world.
Fraudsters pose as a person with whom you have gained trust, an executive of your company, a reputable vendor, an attorney, or government agency. They send a fake request instructing you to wire funds immediately using payment instructions they provide – and they reiterate the urgency of their request. Employees who fear upsetting management, don’t have access to management, or believe they are receiving the request from management, are less likely to question suspicious activity. Unfortunately, the victims don’t realize they have been duped until it is too late. There are countless examples of companies falling victim to wire transfer fraud. The FBI reported that business email compromise (BEC) is more sophisticated than similar scams and has resulted in attempted and actual losses of more than a billion dollars globally.
Wire Fraud Prevention: Identifying Common Wire Transfer Fraud Scenarios
Scenario 1: Business Working With a Foreign Vendor
A business with a long-standing relationship with a vendor receives an email request with new wire transfer instructions to wire funds for an invoice payment. This is an example of a spoof email request; it appears very similar to a legitimate account and would take very close scrutiny to determine it was fraudulent. For example: abuttchen@vendorcompany.com vs. abuttchen@vendorcompony.com. The variation is slight, however, easily and often overlooked. In the event that this request was received via fax or telephone, it would have closely mimicked a legitimate request. This particular scenario has also been referred to as “Invoice Modification Scheme,” “The Supplier Swindle,” or “The Bogus Invoice Scheme.”
Scenario 2: Business Executive Receiving or Initiating a Request for a Wire Transfer
The email account of a high-level business executive (CEO, President, etc.) was compromised. In this case, the email account was spoofed or hacked. An employee responsible for processing payment requests receives a request for a wire transfer from the compromised email account. Without questioning it and concern about bank transfer fraud protection, the employee processes the wire transfer. It is not uncommon for this employee to receive wire transfer requests from the CEO via email. In some instances, a request for a wire transfer from the compromised email account is sent directly to the financial institution with instructions to immediately send funds to another bank for “X” reason. This particular scenario has also been referred to as “CEO Fraud,” “Masquerading,” “Business Executive Scam,” or “Financial Industry Wire Frauds.”
Fraud doesn’t need to happen to your company. You must be proactive about cybersecurity and talk to your trusted treasury management professional about the steps you should take in wire fraud prevention to protect your company.
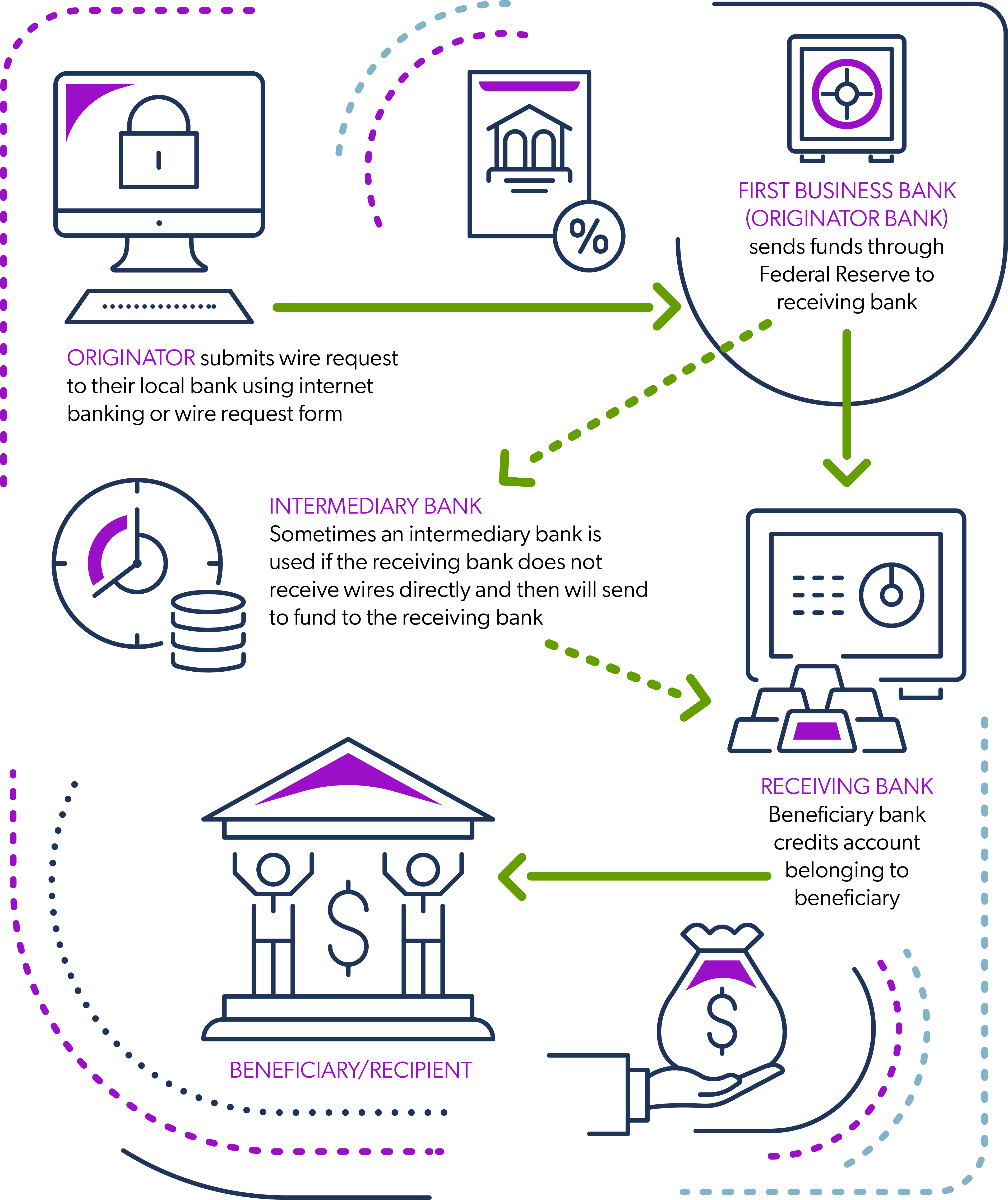
Best Practices On How To Prevent Wire Transfer Fraud:
- Always verify the authenticity of each wire transfer request. Call the person, using a number you have previously called — not one from the current wire transfer request — to verbally verify it.
- Implement a call-back verification process when setting up payment instructions for a new vendor or making changes to payment instructions for an existing vendor.
- Implement dual control and segregation of duties.
- Education is key! Understanding email scams and educating your employees n wire transfer procedures best practices is critical to protect your financial assets.
- Test your fraud health.
- Implement a cybersecurity policy and review it often.
- Review your business insurance policy. Does it cover financial losses due to cybersecurity fraud?





