Account takeover fraud, when a hacker gets into one of your online accounts, is a significant threat to people, organizations, and businesses. In fact, recent data shows that 29% of people, or about 77 million adults, have experienced account takeover fraud. The personal behaviors that can lead to account takeover directly impact businesses, as both employees and customers can unknowingly bring risks into the corporate environment.
Understanding how account takeover fraud happens and implementing effective account takeover prevention strategies is the first step to protect your company's reputation, sensitive information, and financial assets.
What Is Account Takeover Fraud?
Account takeover fraud occurs when criminals gain unauthorized access to a user's account, often through stolen login credentials or social engineering tactics. When they gain control of an account, they can cause extensive damage to your business's finances and reputation.
When hackers access online banking accounts, the stakes are high. Account takeover fraud can lead to:
- Fraudulent payments & transfers
- Reputational damage
- Operational disruptions
- Identity theft
Business Email Compromise (BEC) is a type of account takeover fraud involving criminals accessing work email accounts. This extremely common account takeover fraud allows hackers to:
- Use legitimate email accounts to impersonate executives or finance department employees
- Initiate fake financial transactions
- Redirect legitimate payments to criminal-controlled accounts
- Access sensitive company information
Financial account takeover fraud is different from other types of fraud because of the potential for criminals to cause significant damage over the long term. Unlike isolated incidents, such as a single instance of wire transfer fraud, financial account takeover fraud sometimes continues over a long period of time if it goes undetected. This extended access can lead to sizable financial losses and prolonged identity theft issues.
While financial accounts remain primary targets, cybercriminals also exploit vulnerabilities in corporate cloud storage, employee credentials for government services, company social media profiles, and even business-related subscription services. Social media account takeovers are particularly concerning for businesses and organizations, as they can severely damage brand reputation, erode customer trust, and lead to significant financial and operational consequences.
How Does Account Takeover Fraud Happen?
An important part of account takeover fraud prevention is learning how criminals most often access online accounts, whether business or personal. By understanding their methods, you can work with your IT department to strengthen your prevention strategies and reduce the risk of account takeover fraud at your business.
- Phishing and Social Engineering: One recent study shows that 74% of account takeover attacks begin with phishing. Criminals use misleading emails, phone calls, texts, or social media to trick people into giving them their login credentials or sensitive information. The hackers often pretend to be trusted people, like bank employees, executives, or vendors.
- Credential Stuffing: Every time you make a new account online, you typically have a login username and a password. And every time there’s a data breach involving stolen usernames and passwords, criminals often try to use them to log in to other accounts, sometimes leveraging automated tools to test large numbers of credentials quickly. Unfortunately, many people reuse passwords across multiple accounts, which leaves them vulnerable to account takeover fraud. In fact, only about 12% of adults report making a new, unique password for each account.
The scale of this threat came into sharp focus with a recent discovery of a publicly accessible database with more than 149 million unique usernames and passwords across hundreds of services. The records, compiled by infostealer malware and left unsecured in a cloud repository, includes credentials for Gmail, Facebook, Instagram, and dozens of other platforms. This data gives criminals everything they need to run credential-stuffing attacks across banking, business software, and other corporate accounts.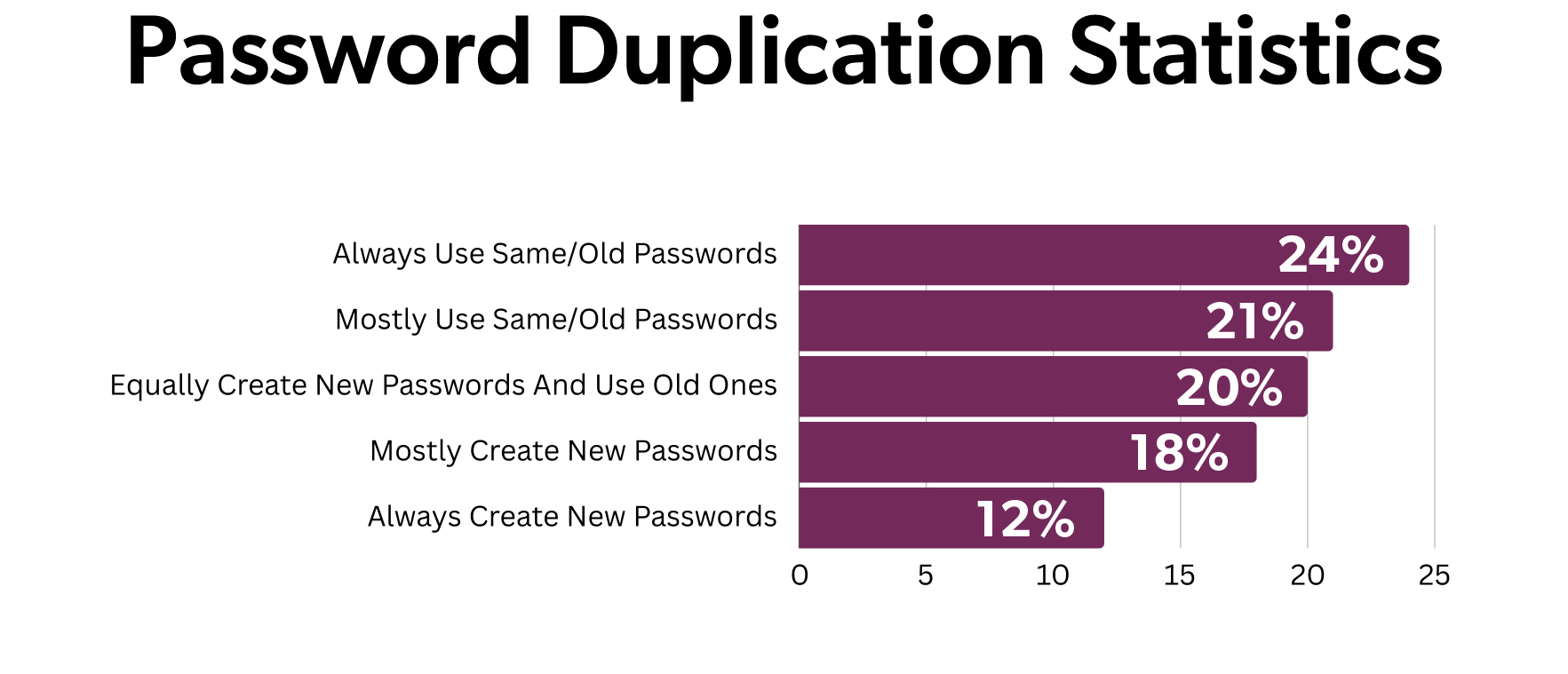
- Malware and Keyloggers: Harmful software programs can get onto your phone, tablet, or computer when you click on links in phishing emails, download suspicious attachments, visit compromised websites, or connect to unsecured public Wi-Fi. Once installed, these programs secretly gather login information and other sensitive data.
- Security Gaps: Weak organizational cybersecurity practices often make accounts vulnerable. These may include weak password policies, lack of multi-factor authentication, outdated software, or insufficient employee training on cybersecurity best practices. Password managers can help employees handle multiple unique credentials, but they carry a risk. High-profile breaches of popular password management platforms in recent years are a reminder that a layered approach works better than relying on any one defense.
What Are Common Signs of Account Takeover Fraud?
Signs that hackers accessed an account will vary by the type of account, but these are some of the most common symptoms of potential account takeover attempts. Pay close attention to anything out of the ordinary.
- Unusual account activity. Watch for unusual account activity like several failed login attempt alerts, transactions that deviate from normal patterns, or logins from unfamiliar locations.
- Alerts from your bank. Financial institutions play a crucial role in detection. They may send alerts about large or out-of-pattern transactions, login attempts from new locations, or changes to account details. Take these notifications seriously and respond promptly.
- Client feedback. Customer complaints can also signal potential fraud. Make sure to investigate further if your customers report unauthorized transactions, difficulty accessing their accounts with you, or unexpected changes to their account information.
How Do Businesses Prevent Account Takeover?
Your business has a duty to implement strong account takeover prevention strategies to reduce the risk of account takeover fraud. Ignoring these can result in major financial losses, damage to your organization’s reputation, and possible legal liability. Prevent account takeover by implementing the following strategies:
- Strong Password Policies: Require your employees to use complex passwords and require ongoing, regular password changes. Do not allow employees to reuse passwords across accounts and encourage them to use password managers to keep track of unique passwords.
- Use Multi-Factor Authentication (MFA): Implement MFA for all accounts, especially those with sensitive information, like online banking. Multi-factor authentication requires a second verification after logging in, such as a code you receive via text, email, or phone call. Consider using biometric authentication or hardware tokens for enhanced security.
- Educate Employees Regularly: Implement a continuous training program to teach your staff to recognize phishing attempts and social engineering tactics. Running simulated phishing campaigns can help reinforce this training.
- Update Software Promptly: Work with your IT department or vendor to regularly update all software, including operating systems, applications, and security software. Apply security patches right away when they're released to reduce risks.
- Monitor Accounts: Reconcile bank accounts daily to promptly catch any unauthorized payments. Work with your bank to implement fraud prevention tools and alerts for unusual account activities.
- Limit Access To Accounts: Only allow employees access to accounts and sensitive information that they need to perform their jobs. Regularly review who can access accounts, especially when employees change roles or leave. Train new employees rigorously on security protocols.
- Upgrade Network Security: Work with your IT department or vendor to implement firewalls and encryption to protect data. Conduct regular security audits and penetration testing. Use network segmentation and VPNs for remote access.
- Review Incident Response Plans: Develop plans to respond to account takeover fraud. Document steps to take, who to contact, and regularly update and test the plan, ensuring all staff members understand their responsibilities.
- Eliminate Single Sign-On For Business Accounts: When employees use single sign-on (SSO) technology to log into a work tool using their Gmail or LinkedIn credentials, you're taking a risk. If one of those accounts is compromised, attackers gain access to everything connected to it. Require separate, unique credentials for every business platform and make this a clear part of your onboarding policy.
- Monitor For Credential Exposure: Regularly check whether your email domains or employee credentials appear in known data breaches using a tool like HaveIBeenPwned.com. Making this part of your routine security checks, rather than waiting for signs of fraud. gives you a head start on changing passwords and locking down accounts before an attack occurs.
Steps to Take When Account Takeover Fraud Occurs
Despite your best efforts to prevent it, account takeover fraud can still happen, and knowing what to do is the first step to fixing it. Criminals often go to great lengths to hide their fraud, including redirecting alerts and notifications to minimize account takeover fraud detection, which means businesses need to be on guard and prepared to act quickly when they suspect fraud. Here are some steps to take:
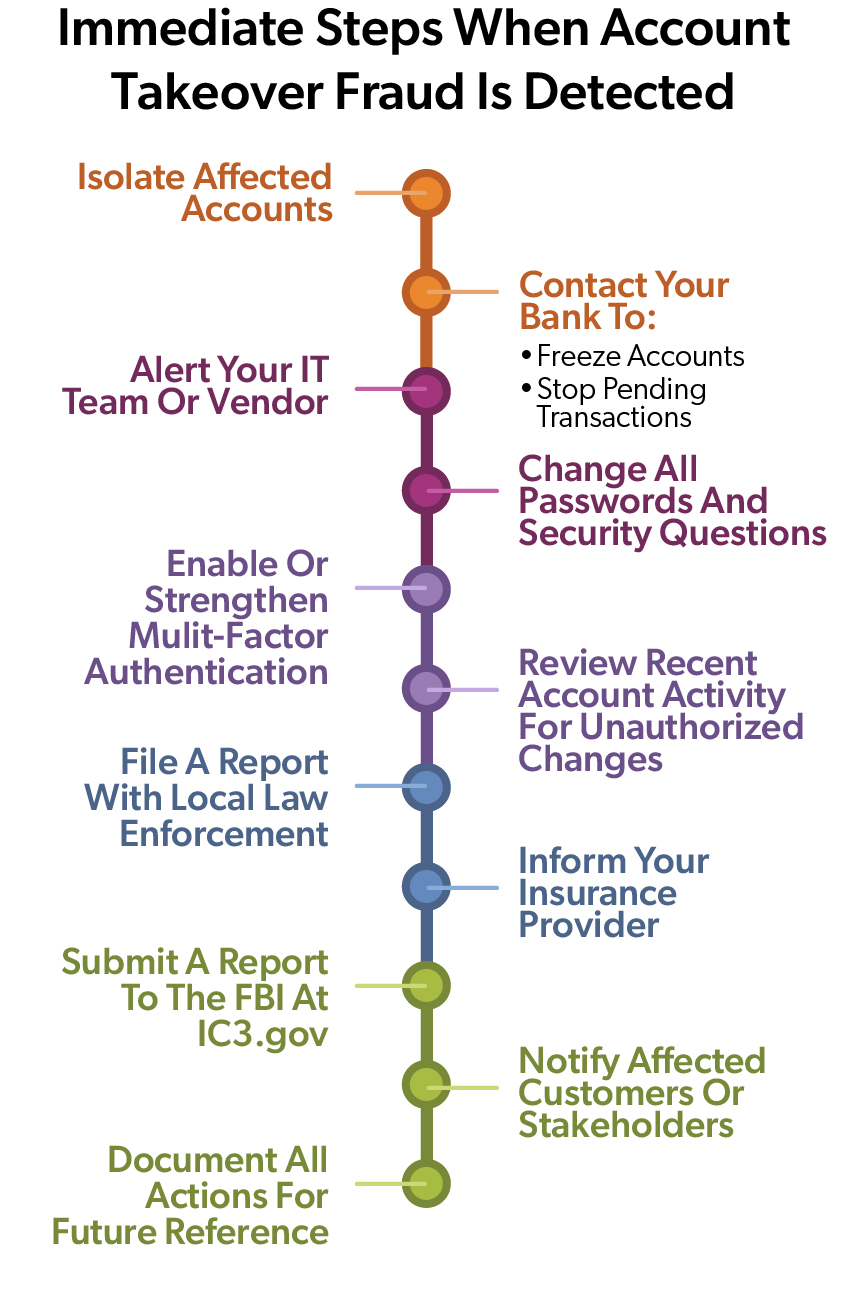
- Act Immediately: Isolate the accounts that are affected and work with your bank to freeze accounts and stop pending transactions. Alert your IT team or vendor, change passwords, enable MFA, file a report with law enforcement, inform your insurance provider, and submit a report to the FBI at IC3.gov.
- Investigate the Breach: Have your IT team or a cybersecurity expert examine the breach in detail. Identify how the attackers gained access, what information was compromised, and determine the timeline of the attack. Collect and preserve evidence for potential legal action. Cybersecurity insurance may cover the cost of this investigation.
- Strengthen Security Post-Breach: Review and update security policies based on lessons learned from the investigation. Implement additional security measures and train employees, including training for the vulnerabilities exploited in the attack.
Strengthening your account takeover fraud prevention strategy is an ongoing process as criminals shift tactics. Massive credential leaks, infostealer malware, and increasingly sophisticated phishing campaigns mean the threat changes constantly. Staying informed, regularly updating your security measures in collaboration with your bank, and building a culture of security awareness across your organization puts you in the best position to minimize risk and limit damages when threats emerge.





