Wire transfer fraud poses a significant threat to businesses of all sizes, with financial losses reaching billions every year. As cybercriminals use increasingly complex tactics, preventing wire transfer fraud has become a critical priority for businesses and organizations.
This article provides decision-makers actionable strategies and best practices to help you safeguard your organization from pervasive and damaging wire transfer scams
We consulted two leaders within First Business Bank: Alicia Anderson, Vice President - Treasury Management and Melissa Fellows, Senior Vice President - Managing Director of Treasury Management. Both experts have decades of experience working with businesses and organizations to help them protect themselves from wire transfer fraud, improve cash flow, reduce overall fraud loss risk, and maximize earnings potential.
What Is Wire Transfer Fraud And How Does It Happen?
In wire transfer fraud, criminals manipulate or deceive individuals or organizations into sending money electronically to fraudulent accounts. Fraudsters like wire transfers because of the ability to send large sums quickly, and because it’s often very difficult to recover the funds.
"Wire transfer fraud is rapidly evolving, and the threat is always growing,” said Anderson. “Criminals constantly change how they operate, so it’s important for organizations to stay up to date on the latest wire transfer fraud prevention strategies. What worked yesterday might not work tomorrow."
How Do Criminals Commit Wire Transfer Fraud?
- Business Email Compromise (BEC): Cybercriminals infiltrate a company's email system, often through phishing attacks that appear like legitimate requests, and use compromised accounts to initiate unauthorized wire transfers. BEC scams are a primary source of wire transfer fraud. Between October 2013 and December 2022, BEC scams accounted for over $50 billion in losses for businesses of all sizes.
- Vendor Email Compromise (VEC): Similar to BEC, in VEC, hackers gain access to a vendor's email account and use it to send authentic-looking invoices to customers with fraudulent payment details. This tactic exploits trusting business relationships to avoid suspicion.
- Fake Invoice Scheme: Without accessing any accounts, scammers create and send out fake invoices that look like legitimate bills but direct payments to criminal-controlled accounts.
- Account Takeover: Account takeover happens when criminals gain direct access to a business's bank account, often through malware or successful phishing attempts in BEC or VEC attacks. With control over the account, they initiate unauthorized wire transfers.
- CEO Fraud: Impersonating high-ranking executives, fraudsters email urgent wire transfer requests to an employee, demanding payment sent to an account controlled by the criminals. To be effective, CEO fraud requires employees to ignore existing wire transfer fraud prevention protocols.
How Do I Recognize the Signs of Wire Transfer Fraud?
Anyone involved in financial transactions of a business or organization can spot the signs of wire transfer fraud. While exact methods are changing all the time, you can learn to recognize wire transfer scams by developing healthy skepticism and a sharp eye for suspicious patterns.
To fight wire transfer fraud, Melissa Fellows emphasized the importance of vigilance. "Wire transfer fraud often succeeds because it exploits human nature — our desire to be helpful, our trust in authority, and our tendency to act quickly under pressure. The key to preventing wire transfer scams is to stop. Verify. Trust your instincts when you feel something is off."
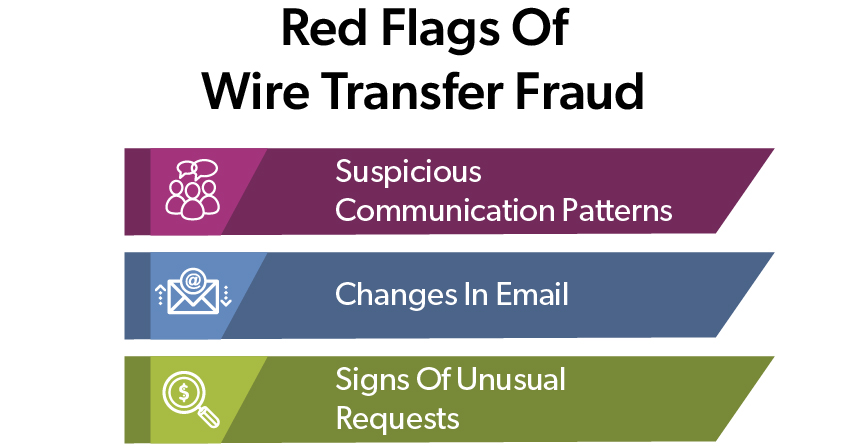
Suspicious Communication Patterns
- Urgent requests for immediate action
- Pressure to bypass standard verification and security procedures
- Unusual timing of requests (e.g., late Friday afternoons or holidays)
- Requests to keep the transaction confidential
Email Red Flags
- Slight variations in sender email addresses (e.g., .com vs .net or 1 vs. I)
- Misspellings or grammar errors in the email
- Generic greetings instead of personalized ones
- Requests for sensitive information via email
Signs Of Unusual Requests
- Changes to current payment procedures
- New or unfamiliar account details for regular vendors
- Requests to wire funds to countries unrelated to the business transaction
- Amounts that differ from typical transaction sizes
How Do I Spot Fake Emails to Prevent Wire Transfer Scams?
Recognizing legitimate vs. fake emails makes all the difference in preventing wire transfer fraud. Here are key strategies to help you find potentially fraudulent email requests :
- Check the full email address, not just the display name. Wire transfer scams often involve fraudsters who use display names that appear legitimate at first glance. Always examine the full email address carefully. Look for subtle misspellings or slight variations from the legitimate address. For example, a scammer might use "ceo@company-name.com" instead of the real "ceo@companyname.com". Be especially skeptical of free email services used for business communications.
- Look for inconsistencies in email signatures or formatting. Legitimate business emails usually have consistent formatting and signatures across the organization. Changes like unusual font choices or sizes, misaligned or missing company logos, inconsistent or missing contact information, and spelling or grammatical errors, should sound alarms.
- Be suspicious of any emailed payment instructions. Never rely only on email to verify new payment instructions or changes to existing payment instructions. Instead:
- Call the sender using a known, previously verified phone number (e.g., from an older invoice)
- If possible, verify new wire transfer payment instructions in person
- Use a secure company messaging system separate from email
- For vendor changes, contact your known account representative, not the person requesting the change.
- Use email authentication tools to detect spoofed emails. Email authentication protocols can help to spot spoofed emails:
- SPF (Sender Policy Framework): Verifies that the sending mail server is authorized to send emails on behalf of the domain
- DKIM (DomainKeys Identified Mail): Ensures that the email content hasn't been tampered with during transit
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): Tells receiving servers how to handle emails that fail SPF or DKIM checks
Work with your IT department or email service provider to ensure these protocols are in place and properly configured. But, even if an email passes these checks, you should still be on your guard. Sophisticated fraudsters can hack into legitimate accounts or systems and send real-looking emails from that system. Always trust your instincts – if something feels off, take the time to verify.
How to Set Up Security Procedures to Prevent Wire Transfer Fraud
Along with spotting fake emails and other signs of wire transfer scams, you’ll want to create and follow security procedures that fit your business or organization. A knowledgeable banker can review them, as well. Here’s a starting point to help you begin setting up strong measures to prevent wire transfer fraud.
- Establish a Clear Chain of Authority
- Choose specific people who can initiate and approve wire transfers
- Implement dual control, requiring two separate approvals for transfers above a certain dollar amount
- Create a Verification Process
- Develop a standardized procedure for verifying all wire transfer requests
- Include multi-factor authentication for digital approvals
- Establish a callback procedure using pre-verified phone numbers
- Set Up System Controls
- Configure your banking platform to flag unusual activity
- Set daily limits on wire transfer amounts
- Implement IP restrictions to limit access to authorized locations
- Develop Written Policies and Procedures
- Document all wire transfer processes in detail
- Include steps for handling exceptions or emergency situations
- Regularly review and update these policies
- Implement Secure Communication Channels
- Use encrypted email or secure portals for sharing sensitive information
- Avoid using public email services for financial communications
- Establish Vendor Management Procedures
- Implement a formal process for changing vendor payment details
- Require multi-step verification for any changes to existing vendor information
- Train Your Team
- Conduct regular training sessions on wire transfer security for all relevant staff
- Include simulations of fraud attempts to test and reinforce protocols
- Set Up Monitoring and Auditing Processes
- Regularly review wire transfer activity for any anomalies
- Regularly audit your wire transfer processes to take the opportunity to update them with new recommendations
- Create an Incident Response Plan
- Develop a clear plan of action in case of suspected fraud
- Include contact information for bank representatives, law enforcement, and internal stakeholders
- Leverage Banking Security Features
- Work with your bank to implement additional security measures they offer
- This may include Positive Pay, Check blocks, ACH Positive Pay, ACH blocks, Account Reconciliation, multi-factor authentication (MFA), or fraud detection services
What Should I Do If I Suspect Wire Transfer Fraud?
Detecting wire transfer fraud can be shocking, but it’s very important to act quickly and follow a set of guidelines you develop for your organization in advance. Many banks can only try to recall funds up to 24 hours. Beyond that time, it’s much more difficult to get your money back.
"I advise clients to have a clear, well-practiced response plan,” Anderson said. “In cases of suspected fraud, every minute counts. The faster you act, the better your chances of minimizing losses and aiding recovery efforts."
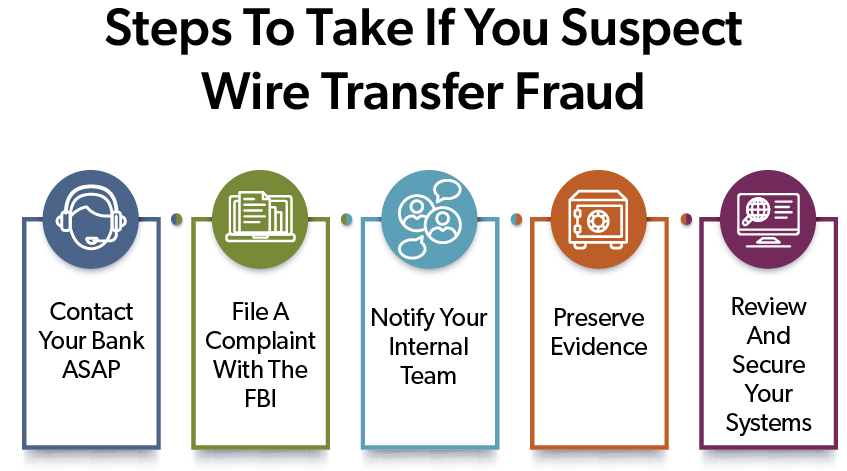
Immediate Steps to Take If You Detect Wire Transfer Fraud
- Contact Your Bank Immediately
- Inform your bank of the suspected fraudulent transfer
- Request an immediate recall of the money
- File a Complaint with the FBI
- Submit a report to the FBI’s Internet Crime Complaint Center (IC3)
- Make sure to provide all the details of the transaction in your report
- Notify Your Internal Team
- Alert your IT department to potential security breaches
- Inform executives who need to know and legal counsel
- Preserve Evidence
- Save all communication related to the wire transfer fraud
- Document the timeline of events for the investigation
- Review and Secure Your Systems
- Change passwords and credentials
- Work with your IT department or vendor to scan systems for malware or unauthorized access
How Often Is Money Returned From Wire Transfer Scams?
The chances of wire transfer fraud recovery vary, and getting everything back is often difficult.
"In wire transfer fraud cases, the faster you detect and report the fraud, the higher your chances of recovery,” Fellows said. Even with quick action, though, it’s not always possible to get every dollar back."
Several factors influence the likelihood of wire transfer fraud recovery :
- Speed of detection, response, and reporting
- Where the funds went (domestic vs. international)
- Cooperation of receiving banks
"Implementing strong preventive measures is your best defense against wire transfer fraud losses,” Fellows said. “It's much easier to stop fraud before it happens than to recover funds after the fact."
What Happens After Wire Transfer Fraud?
The aftermath of wire transfer fraud involves a complex process of investigation and possible legal consequences.
"When you report wire transfer fraud, an investigation begins,” Anderson said. “This often involves financial forensics, digital evidence gathering, and collaboration with law enforcement agencies."
Wire transfer fraud investigations typically involve:
- Financial Forensics: This step focuses on tracing the path of funds and analyzing transaction patterns to identify any irregularities or suspicious activities.
- Digital Evidence Gathering: Investigators examine email communications and investigate potential system breaches to understand how the fraud was executed and identify any vulnerabilities in the system.
- Collaboration with Law Enforcement: This involves working with local police and federal agencies, as well as possibly international entities for cross-border wire transfer fraud cases .
"These investigations can be time-consuming and complex, especially when they cross international borders,” Anderson said. “In my experience, patience and persistence can make a difference. The difference can mean some financial recovery as opposed to a total loss."
Legal Considerations for Businesses After Wire Transfer Fraud
While businesses aren't typically held legally liable for falling victim to wire transfer fraud, there can be indirect consequences like civil litigation, regulatory scrutiny, reputational damage, and loss of client trust.
"Strong wire transfer fraud prevention protocols help to protect your assets and demonstrate due diligence,” Fellows said. “This can help mitigate potential legal and regulatory issues down the line."
Should My Business Have Cybersecurity Insurance For Wire Transfer Fraud?
When it comes to replacing funds from wire transfer fraud, cybersecurity insurance can provide a safety net.
"We always emphasize prevention, but insurance can be an additional layer of protection,” Anderson said. “Cybersecurity insurance is part of a comprehensive risk management strategy, especially given the potentially devastating impact of wire transfer fraud."
The Importance of Adequate Coverage For Wire Transfer Fraud Losses
Cybersecurity insurance policies can help ease the financial losses associated with wire transfer fraud. These policies sometimes cover:
- Financial losses from wire transfer fraud
- Legal expenses related to wire transfer fraud investigations
- Costs associated with notifying affected parties
- Expenses for public relations efforts to manage reputational damage
Every business has unique needs and risk profiles, given their industry, size, and other factors. Anderson recommends working closely with your insurance partners to figure out the right coverage for your organization.
“Cybersecurity insurance often comes with access to expert resources that can help you respond quickly and effectively in the event of a fraud attempt, potentially minimizing your losses,” Anderson said.
Establishing internal measures to prevent wire transfer fraud is the most important, but the complexity of this fraud requires an expert banking partner. Expert Treasury Management bankers can provide you with valuable resources, the latest technology, and up-to-date recommendations to protect your business. In the fight against wire transfer fraud, a skilled banking partner is your strongest ally.






